SHA 256: Compute a SHA 256 hash using C# for effective security - .Net Core | MVC | HTML Agility Pack | SQL | Technology Crowds
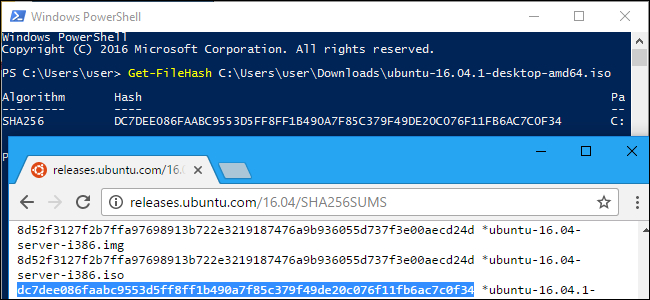
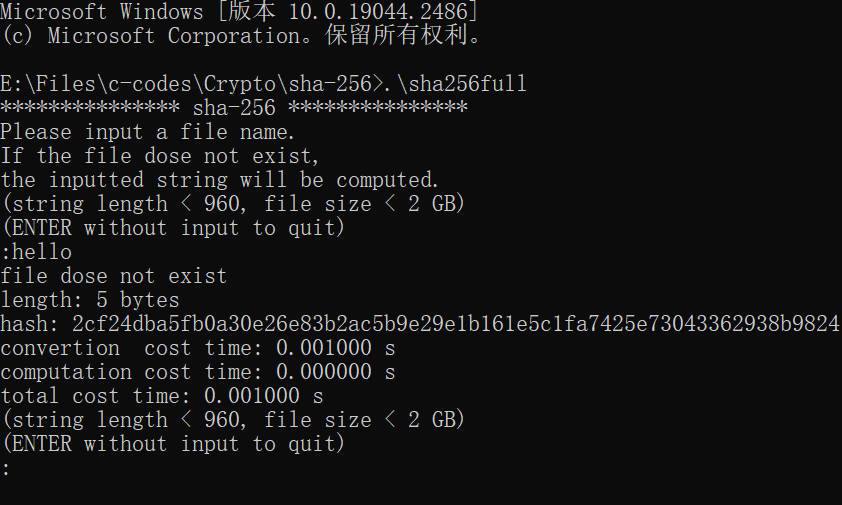
How to Verify the Authenticity of a File Using SHA256 – Battle For America's Spirit – The Real His-Story of Josiah David and Dennis Lee
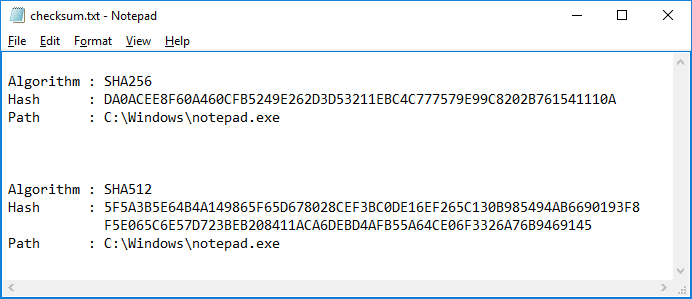
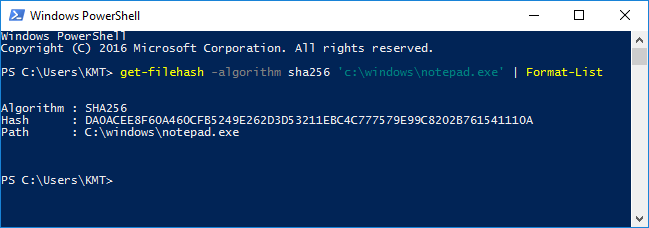
How do you determine the SHA-256 or SHA-512 checksum of a file? - ID: 109483101 - Industry Support Siemens