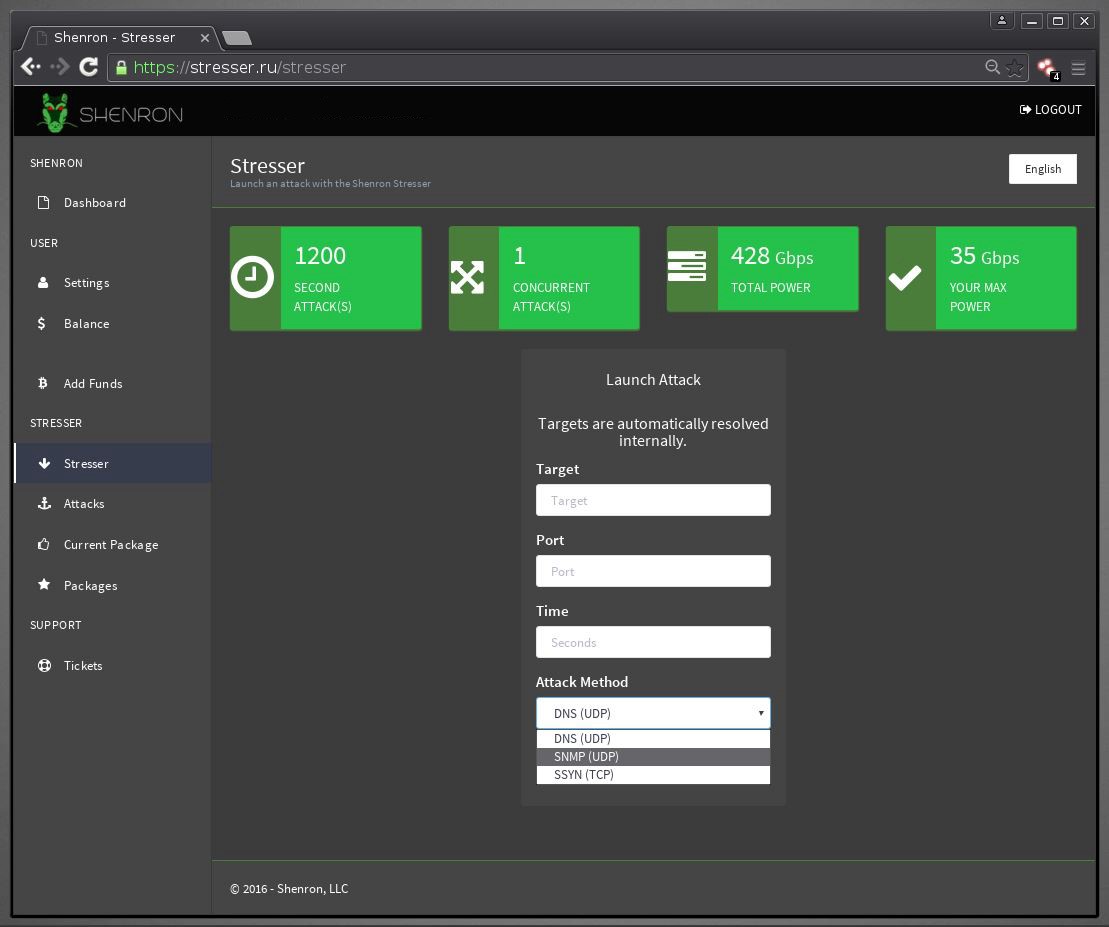
How NETSCOUT built a global DDoS awareness platform with Amazon OpenSearch Service | AWS Big Data Blog
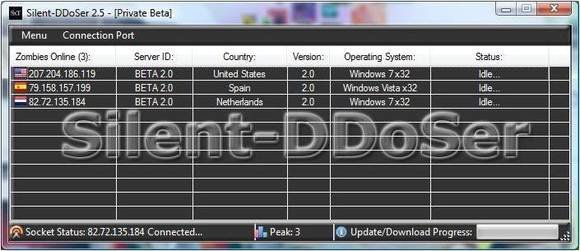
A screen grab of the software program known as the Low Orbit Ion Cannon used by the Anonymous hacker group for Distributed denial of service (DDOS) attacks on websites Stock Photo -
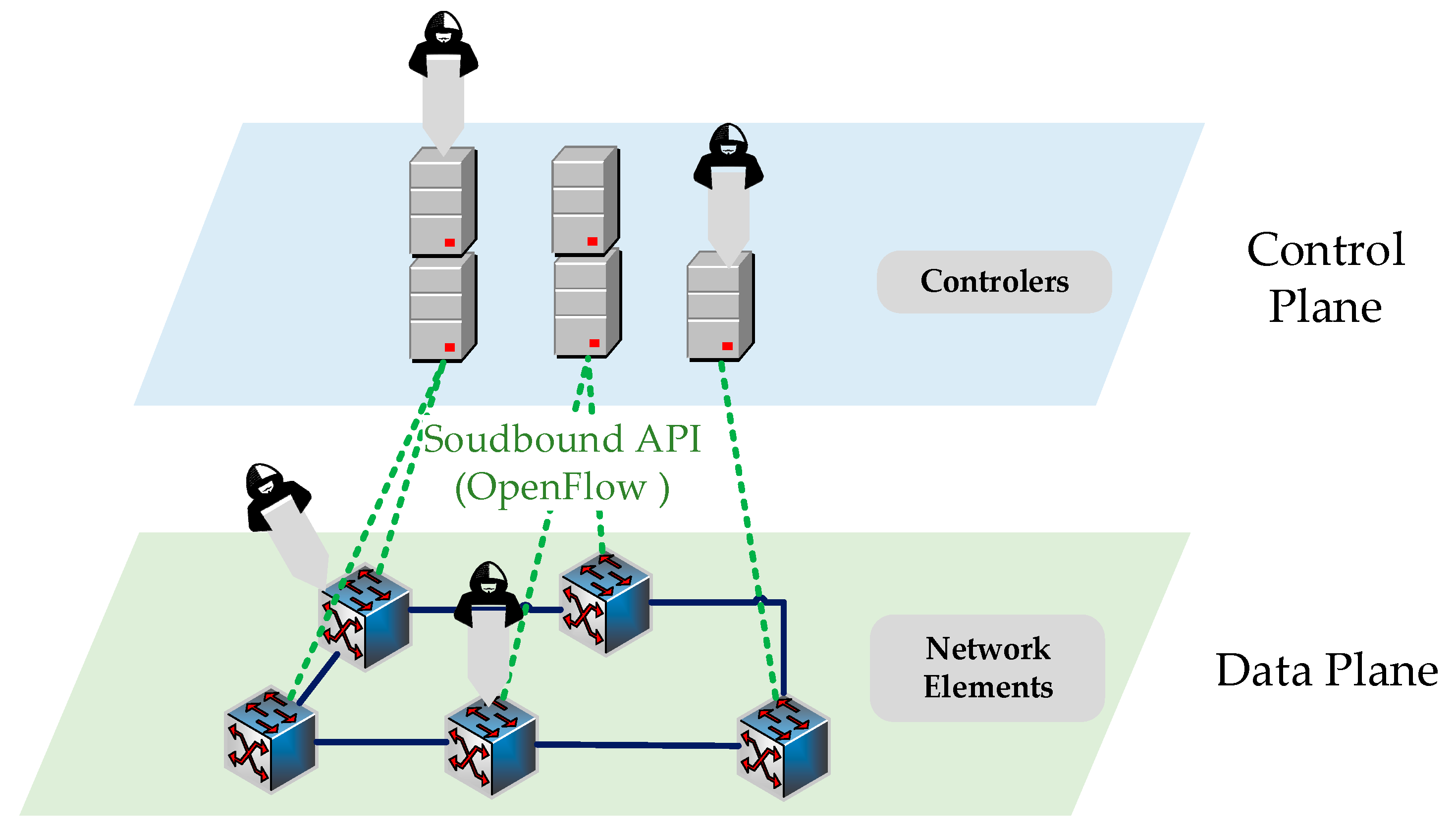
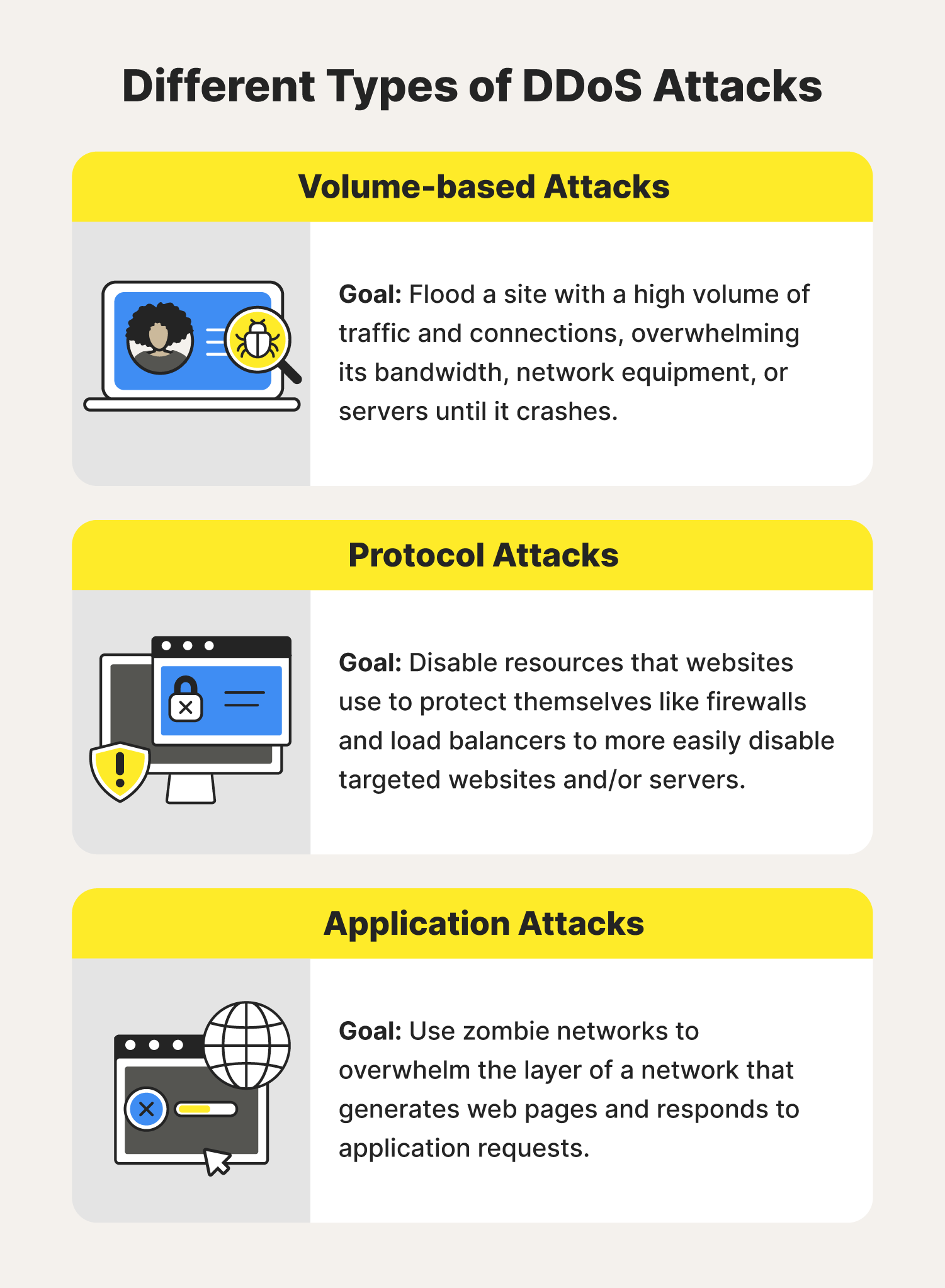
Sustainability | Free Full-Text | Detecting DDoS Attacks in Software-Defined Networks Through Feature Selection Methods and Machine Learning Models
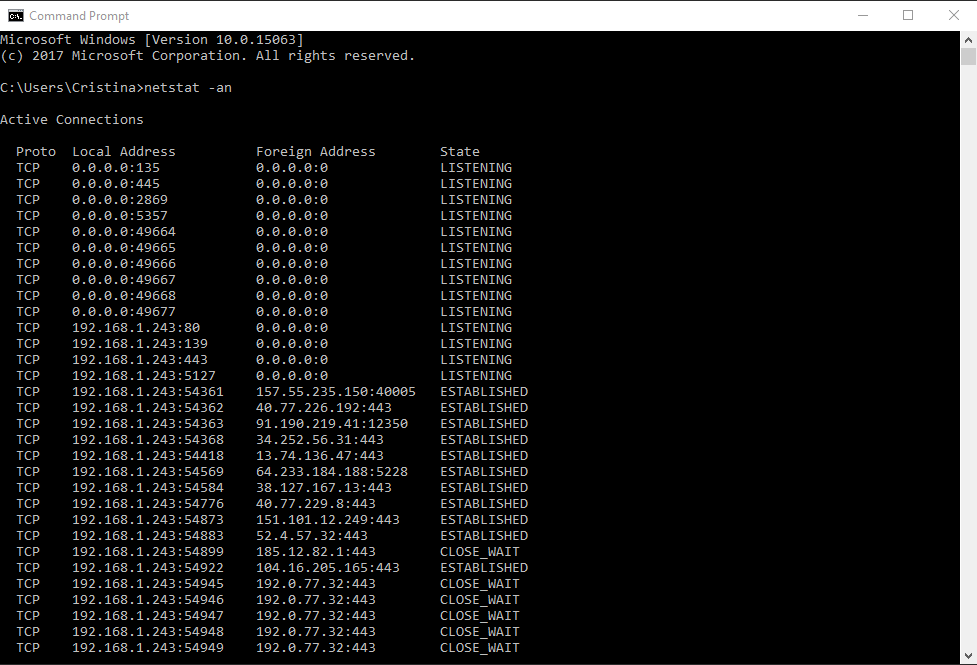
![Understanding DoS attacks and the best free DoS attacking tools [updated in 2020] | Infosec Resources Understanding DoS attacks and the best free DoS attacking tools [updated in 2020] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/2-364.png)