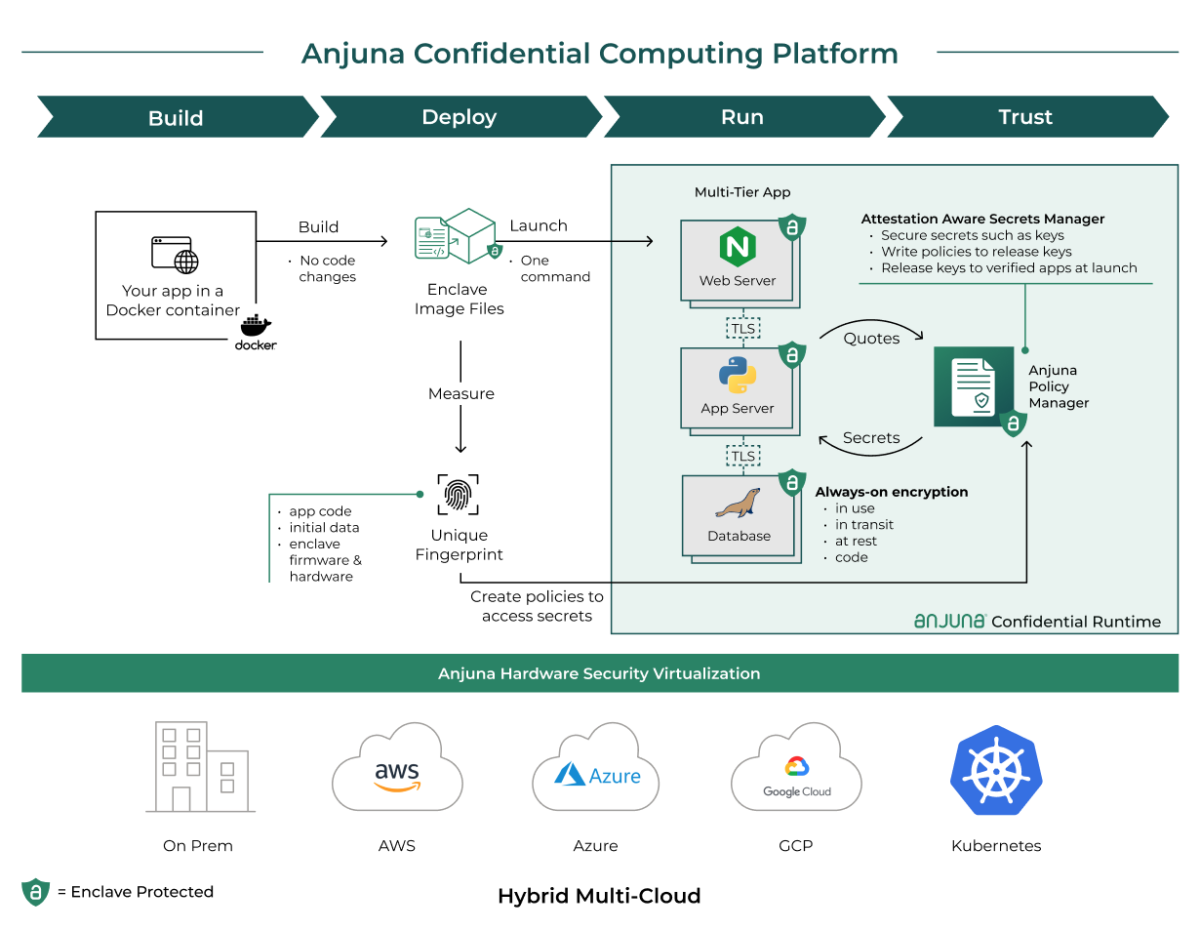
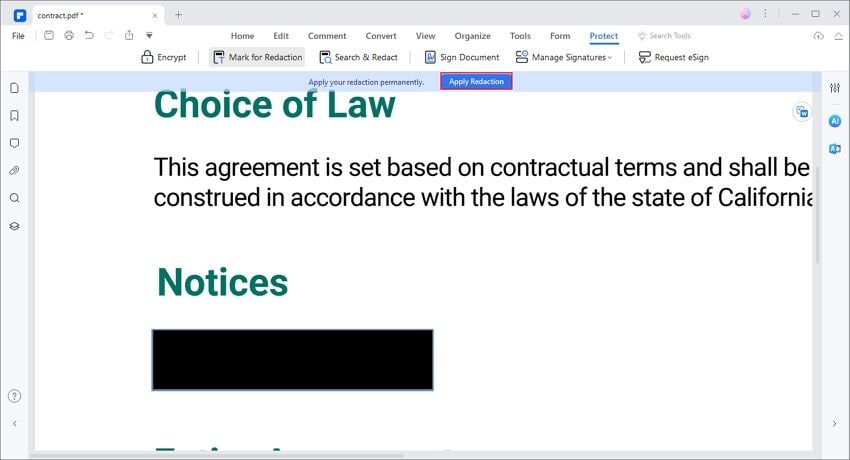
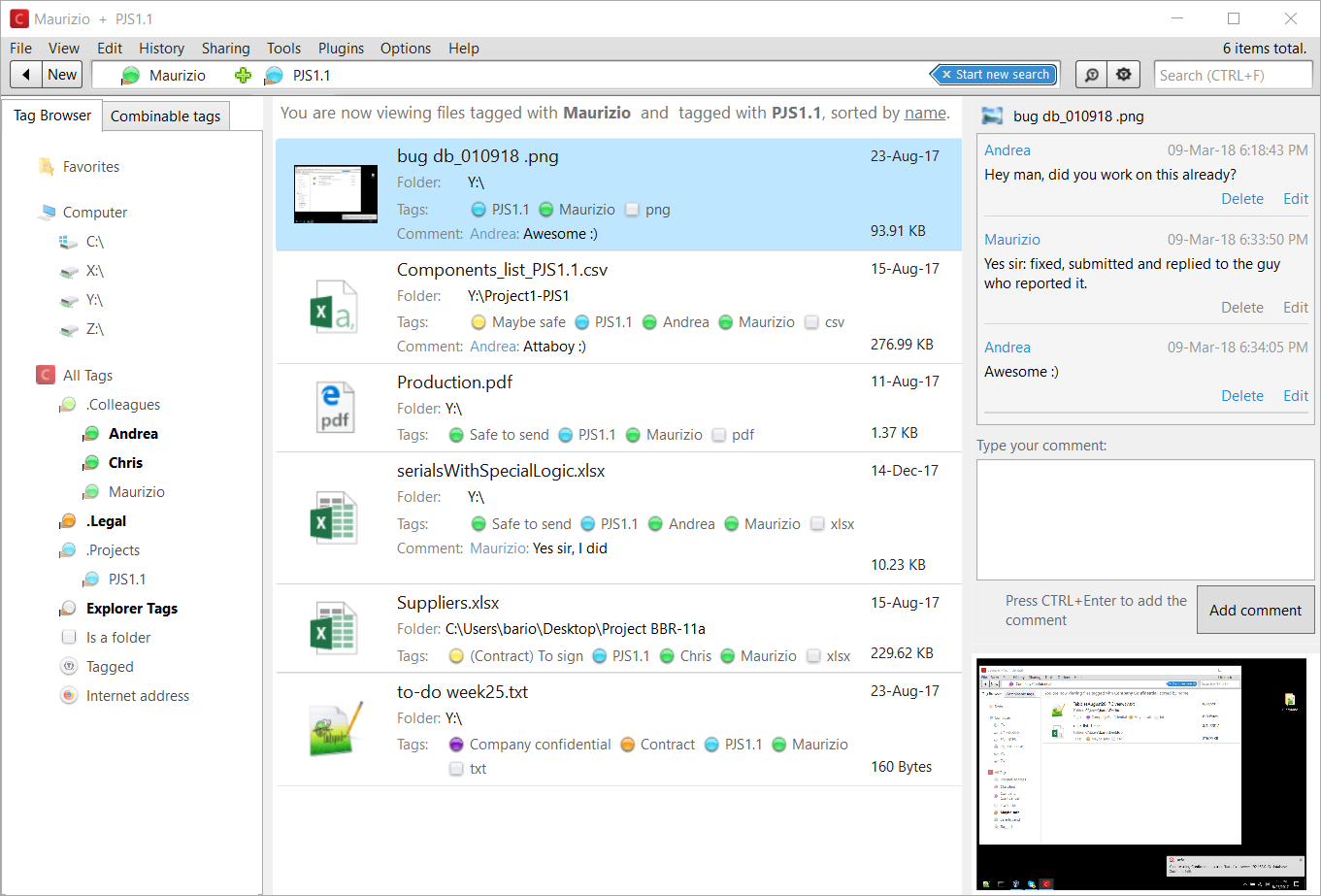
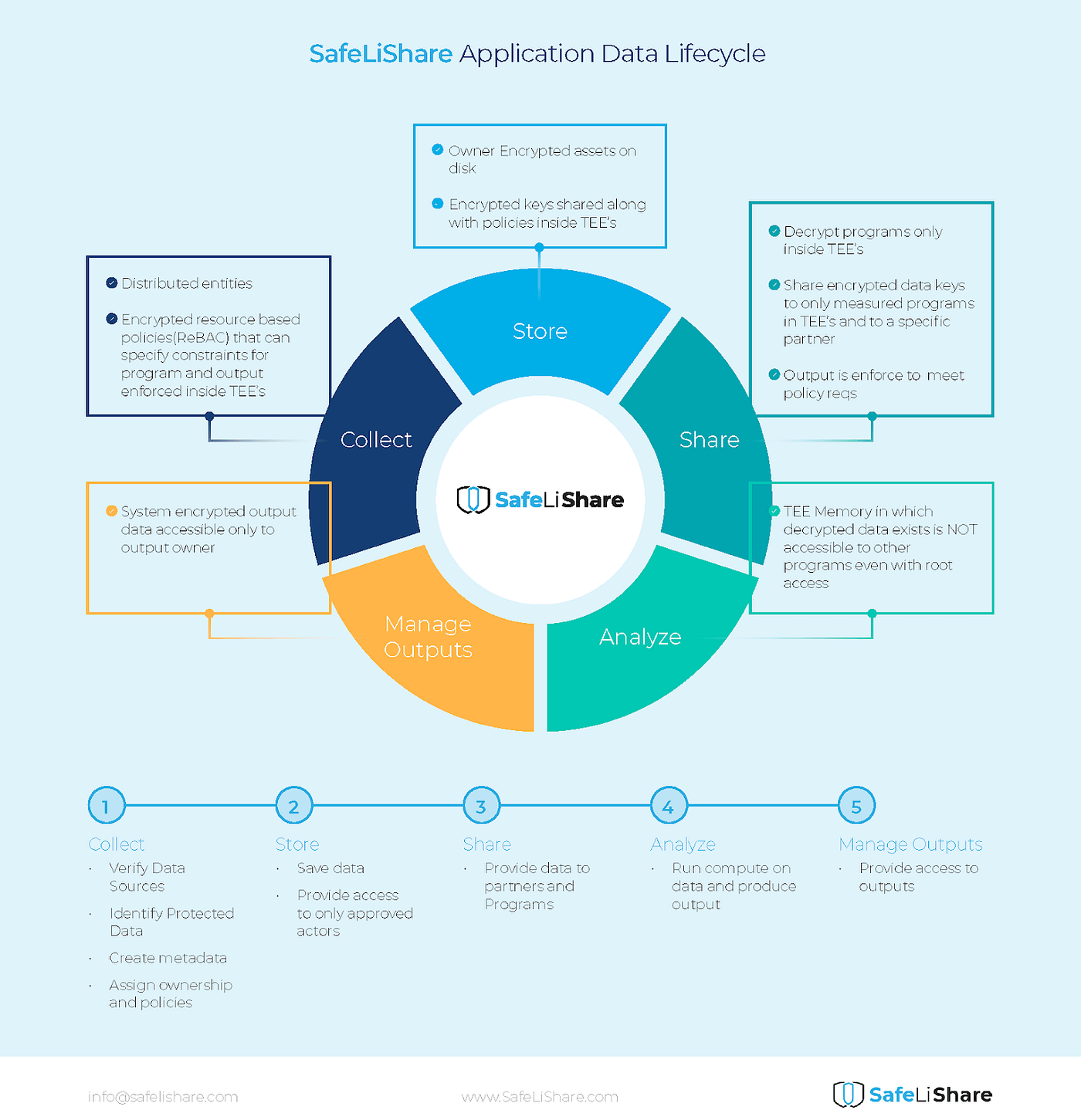
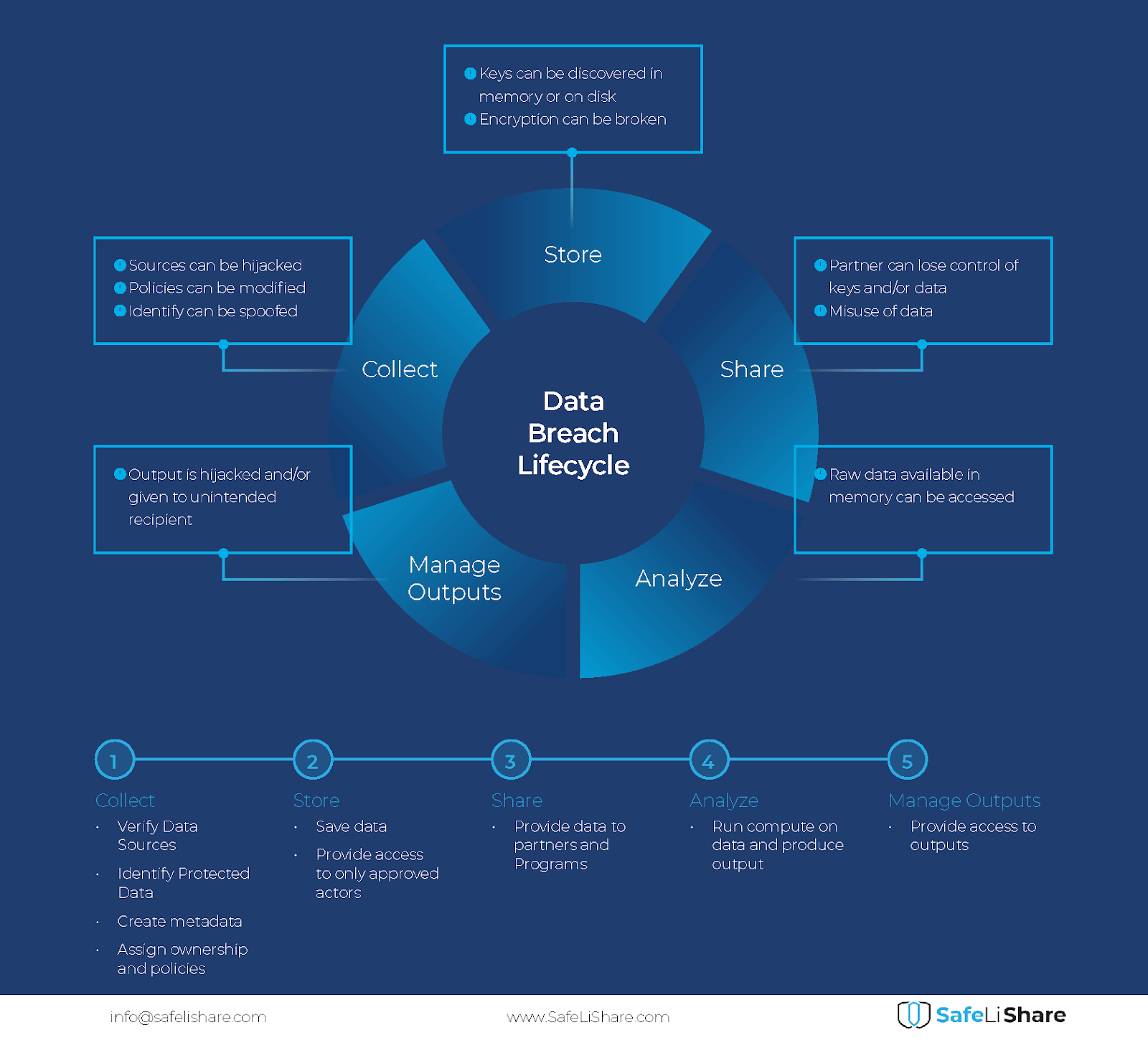
Data Protection Concept. Credit Card Check and Software Access Data As Confidential Stock Vector - Illustration of hacker, cyber: 159744932

Software Development Non Disclosure Agreement | PDF | Proprietary Software | Non Disclosure Agreement

Azure Confidential Computing updates with Mark Russinovich | Best of Microsoft Ignite 2018 - YouTube